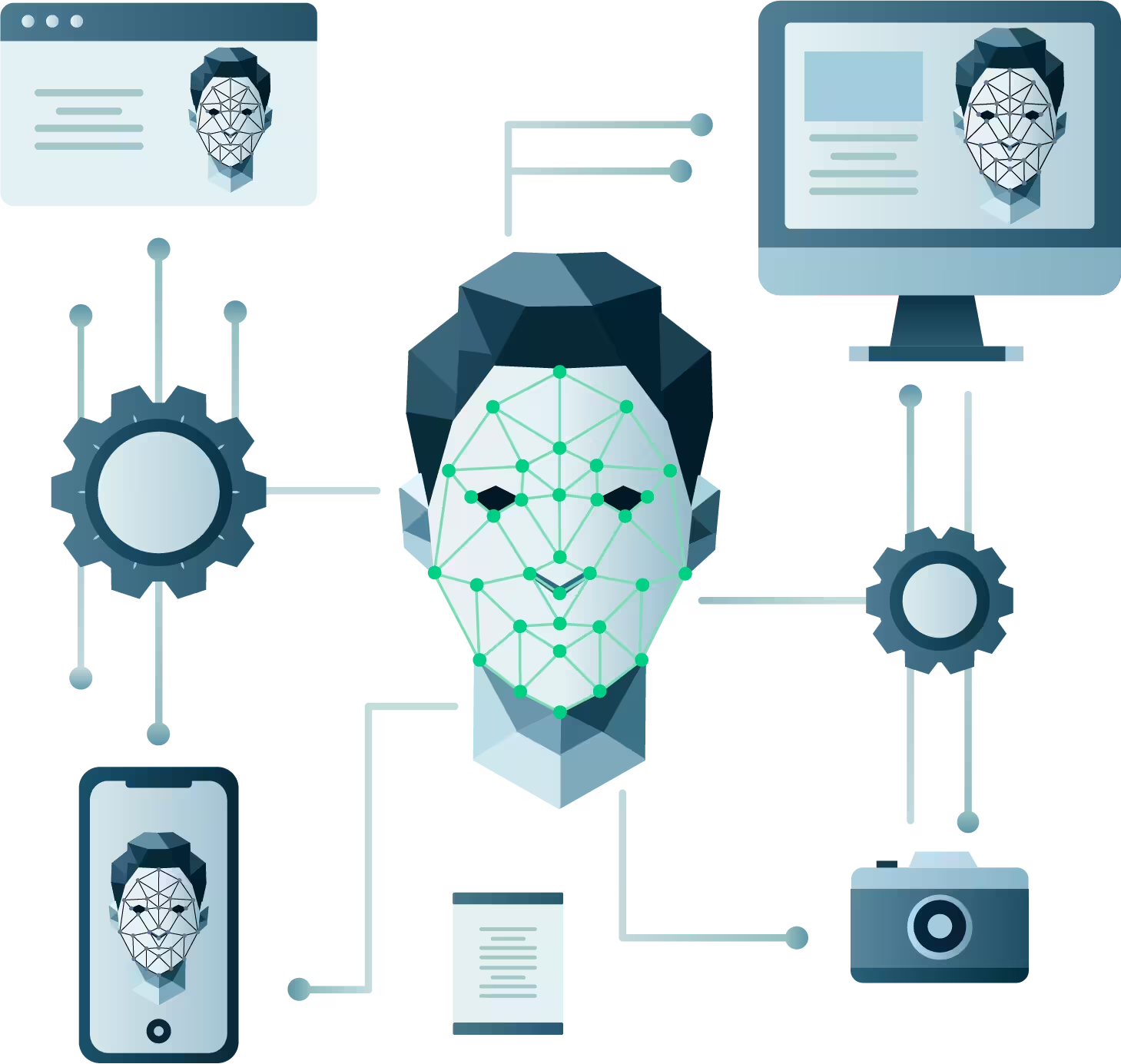
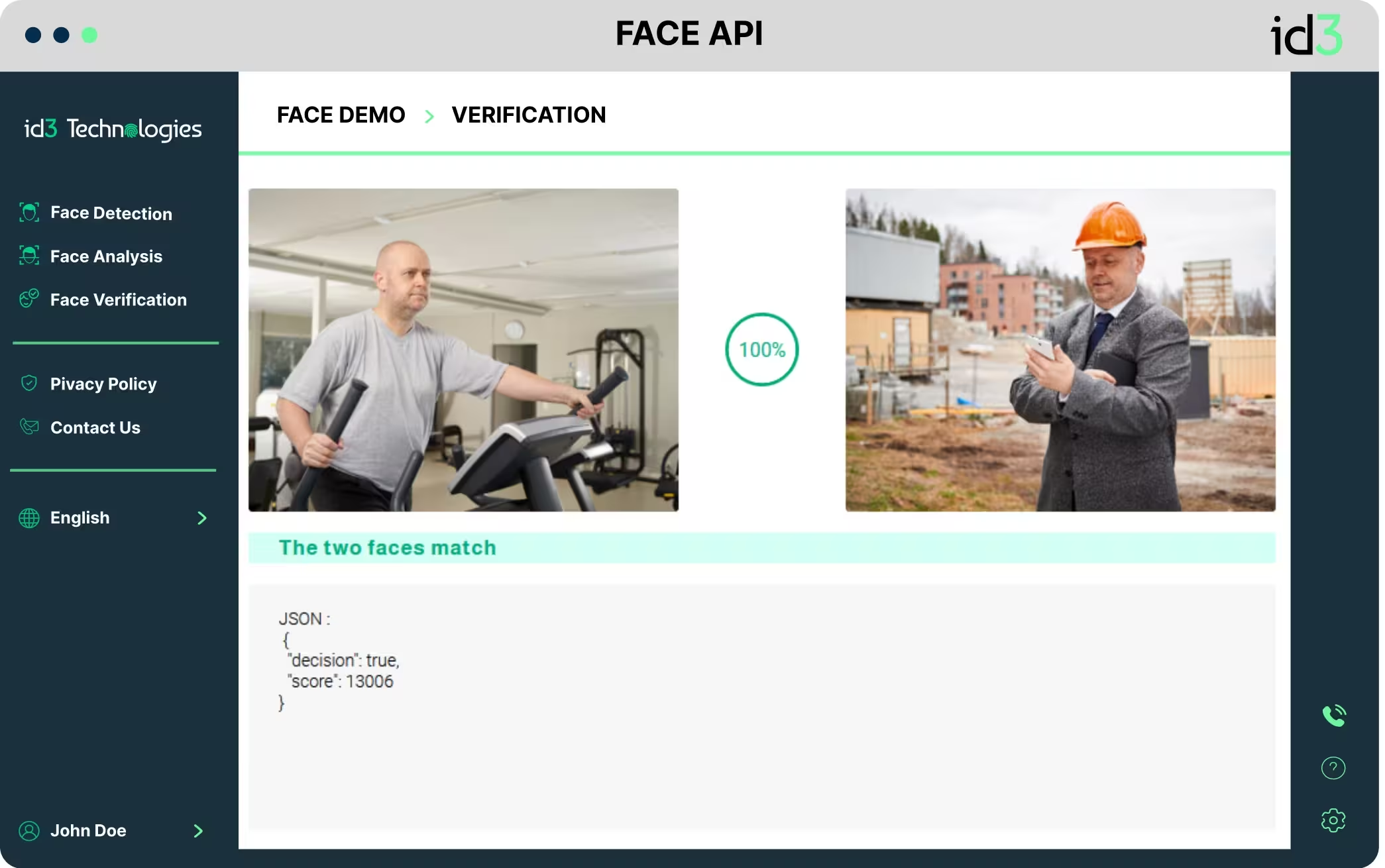
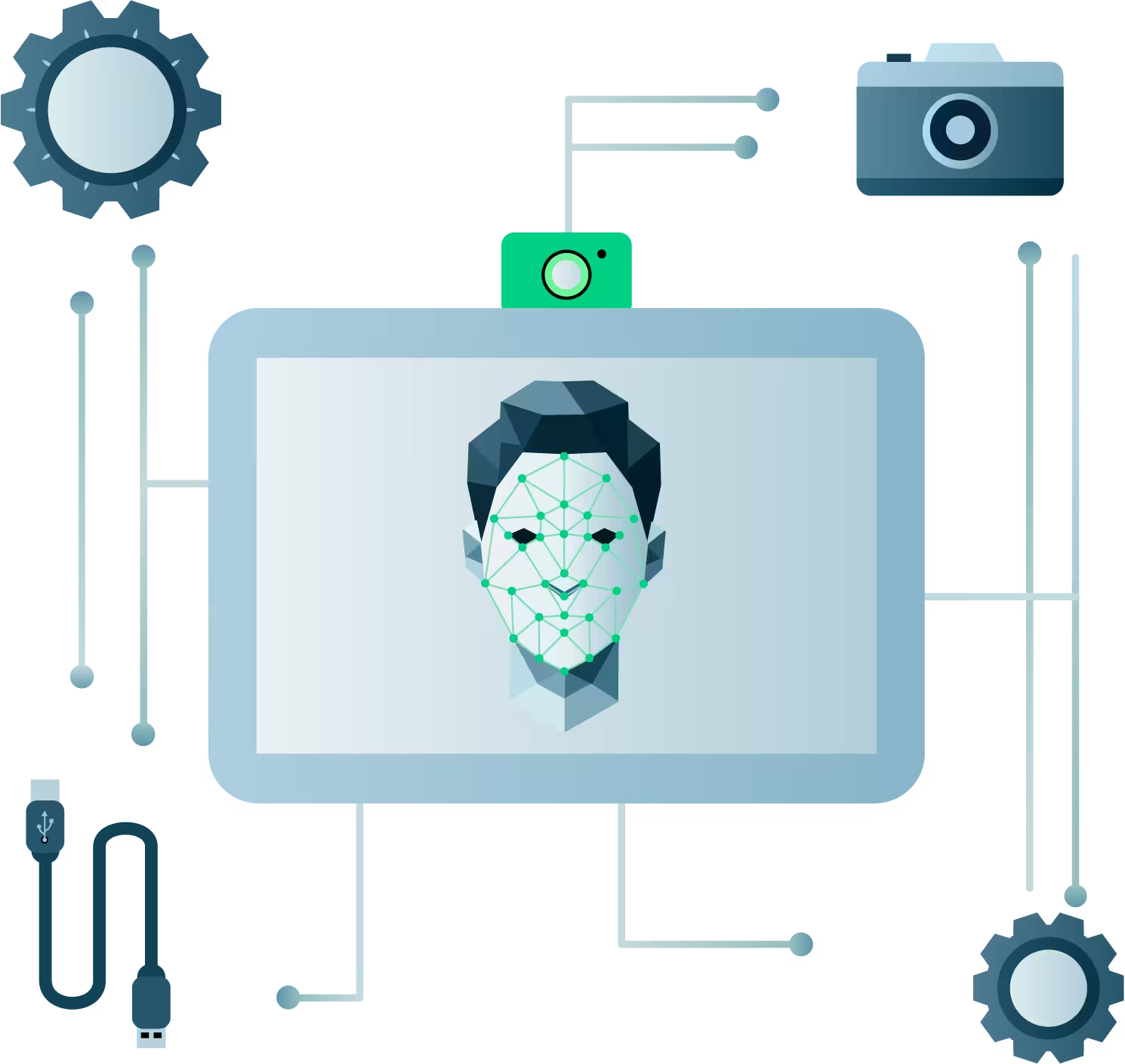
Face recognition is the most efficient identification technology.
Face recognition technology is an application of artificial intelligence and computer vision that automates the identification and verification of individuals from digital images or video frames. This technology leverages biometric analysis by mapping facial features from a photo or video and comparing them to databases to find matches, providing significant benefits in security, personal identification and access control across multiple sectors.
How it works.
face recognition
Face recognition involves several key steps, starting with face detection to locate human faces in images. It then analyzes and extracts unique facial features using advanced algorithms and neural networks. This process transforms facial data into a digital representation, allowing comparison to a stored database for authentication purposes. Thus, it’s a powerful tool for enhancing security systems.
Enhance security
More secure than traditional methods because it relies on biometric data that is unique to each individual.
Fast authentication
Experience real-time identification with our system’s ability to quickly process and match facial data.
User friendly
A non-intrusive authentication method that provides an easy-to-use, contactless alternative to traditional security methods.
Why choose us?
Technology performance.
Lightweight and fast AI models.
Our AI models stand out for their lightweight design and rapid processing capabilities. These models enable fast, accurate facial recognition, and operate efficiently even on devices with limited computing resources. As a result, this makes them ideal for a wide range of applications where speed and efficiency are paramount.
Software integration.
Cross-platform compatibility.
Our face recognition technology integrates seamlessly across a diverse range of platforms. Moreover, it operates efficiently within various hardware environments, from high-end servers to low-resource microcontrollers. Therefore, this cross-platform compatibility ensures that our solutions meet the evolving needs of the technology landscape.
Data privacy.
Data security and compliance.
While facial recognition technology offers many benefits, it also raises concerns regarding privacy. In fact, one major concern is the collection and storage of biometric data. Indeed, there is a risk that hackers could access or use this data without consent. Consequently, this could lead to potential privacy breaches. Thus, id3 Technologies prioritizes user privacy and data protection. So, our face recognition technology adheres to stringent data protection regulations. Further, we ensure that all biometric data is processed or stored with the utmost security and ethical considerations. Finally we have created the Match-on Card, the most secure biometric authentication technolgy on the market.
Applications
Access control
Provides a secure, efficient, and contactless way to verify identities, preventing unauthorized entry and ensuring safety.
Law enforcement
Quickly identifes suspects, locating missing persons, and verifying identities, thereby improving public safety and efficiency.
Online authentication
Enhances online authentication by providing a secure, convenient, and quick way to verify user identities, reducing the risk of fraud and unauthorized access.
Healthcare
Streamlines patient identification, improves access to medical records, and ensures accurate treatment, thereby increasing efficiency and patient safety.
Reliable technology proven in a world-renowned NIST evaluation.
id3 Technologies face recognition algorithm has proven excellent tradeoff between accuracy, speed and template size in the NIST ongoingFace Recognition Technology Evaluation (FRTE). The FRTE was initiated by the National Institute of Standards and Technologies (NIST) in February 2017. It is aimed at measurement of the performance of automated facial recognition technologies applied to a wide range of civil, law enforcement and homeland security applications including verification of visa images, de-duplication of passports, recognition across photojournalism images, and identification of child exploitation victims.